Besa Mafia: The dark web’s murder-for-hire scam
The operation revealed how the boundaries between digital deception and physical violence could blur
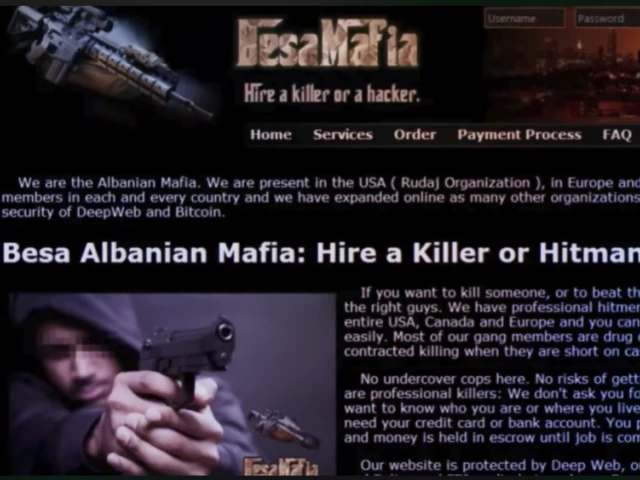
The Besa Mafia operation stands as one of the most revealing cases in the evolution of dark web criminality, a fake murder-for-hire service that escalated from online fraud to real-world tragedy. Hosted on the anonymizing Tor network, the site was not a genuine criminal syndicate but a scam built to siphon cryptocurrency from individuals seeking to commission murders.
Originally exposed by independent cybercrime researcher Chris Monteiro, the operation revealed how a fabricated online brand could blur the boundaries between digital deception and physical violence. The story was first reported by Wired in 2018 and later revisited by the YouTube investigator Scammer Payback yesterday.
A business model built on fear
At the center of the operation was a man known only as “Yura.” He built multiple websites under names like Besa Mafia, Crime Bay, and Camorra Hitman, claiming to offer assassination services in exchange for Bitcoin payments ranging between $5,000 and $20,000.
In reality, Yura never employed hitmen. He lured users into paying large sums, then fabricated excuses for delays, often claiming a “hitman was arrested”, while pushing them to pay even more for “professional” killers.
Read: Halo comes to PlayStation, signals a new direction for Xbox
Despite being a scam, the illusion of violence was convincing. Yura hired freelancers to boost the site’s visibility through SEO campaigns and micro-websites that both condemned and promoted Besa Mafia, creating a cycle of online reinforcement. Some accomplices even produced staged “proof” videos of violence, including one where a car was set on fire and dedicated to a critic’s blog.
The researcher who exposed it
Monteiro’s investigation began in 2016 when he found a link to Besa Mafia inserted into a RationalWiki article. After exposing it as a scam on his blog, he received direct threats, including the infamous burning-car video.
Using his technical expertise, Monteiro infiltrated the operation, collected internal data, and published his findings online. His research revealed hundreds of real murder plots commissioned by users, forcing him into the uneasy role of informant.
“The clients were the dangerous ones,” Monteiro told Wired. “The people using the site wanted others dead, even if the service was fake.”
Law enforcement lagged behind
Monteiro’s attempts to alert authorities highlighted the challenges of policing decentralized cybercrime.
Early reports to London police and the UK’s National Crime Agency (NCA) went largely unanswered due to jurisdictional confusion. The FBI referred him back to British authorities, while warnings sent through Interpol lost critical context, rendering them ineffective.
In a bizarre twist, Monteiro himself was arrested in 2017 after Yura planted false information online framing him as the site’s operator. He was released after two days when evidence proved he had been investigating the scam.
Despite bureaucratic setbacks, Monteiro’s findings later assisted US Homeland Security and Romania’s Directorate for the Investigation of Organized Crime and Terrorism (DIICOT) in tracking down the group behind the scheme. In 2022, five men in Romania were arrested in connection with the network.
Digital deception, real death
The psychological and physical fallout of the scam was devastating.
In 2016, Stephen Allwine, a Minnesota man, attempted to hire a killer for his wife, Amy, through Besa Mafia. When the plan failed, he murdered her himself. He was sentenced to life in prison.
Other targets were less fortunate: Bryan Njoroge, a US soldier, was found dead under suspicious circumstances in 2018 after someone used the site to order his killing. Many victims who survived suffered lasting trauma after learning someone had placed a bounty on their lives.
By 2022, data from Monteiro’s investigation had led to at least 25 arrests and over 30 convictions across multiple countries, including Denmark and the United States.
An enduring threat
Despite the 2022 arrests, the model pioneered by Besa Mafia continues to inspire copycats. Dark web channels like the so-called “Jabba Syndicate” have re-emerged, quoting prices as high as $15,000 per contract.
Also read: Gray imports fill Pakistan’s gadget gap but at the buyer’s expense
Cybersecurity experts warn that the danger lies not in the technical capability of such sites but in the intent of their users. “Even if the service is fake, the intent is real, and that’s what turns digital threats into physical crimes,” one analyst said.
Immediate public plans regarding the Kill List
Carl Miller is now preparing for a major public disclosure and call to action at a prominent security conference. He is scheduled to give a talk on the Kill List at Defcon. At the end of his talk, he plans to reveal new information that has not been publicly shared before.
He intends to disclose that, on behalf of Chris Monteiro, of the 175 paid kill orders that they previously focused on, there are at least 2,000 other kinds of orders that have never been properly analyzed or investigated. Carl intends to reach out to the world of hackers at Defcon.
He plans to ask who is willing to help look at this vast dataset to see whether new investigations can be set up or new information can be learned.



















COMMENTS (1)
Comments are moderated and generally will be posted if they are on-topic and not abusive.
For more information, please see our Comments FAQ