Microsoft Windows can be hacked with a single unread email: Google
Microsoft has issued a fix after it was discovered by Google researchers

The Microsoft logo is seen on an electronic billboard on an office building in New York City, July 28, 2015. PHOTO: REUTERS
Over the weekend, Ormandy and Silvanovich announced their discovery on Twitter causing fears that users were susceptible to attacks over email.
I think @natashenka and I just discovered the worst Windows remote code exec in recent memory. This is crazy bad. Report on the way.
— Tavis Ormandy (@taviso) May 6, 2017
It is a particular cause for concern as it can compromise your system without the user even opening or reading the full email.
Microsoft was made aware of the issue and finally on Tuesday it responded with a fix for the flaw with a critical update which patches the loophole.
Microsoft launches stunning new Surface laptop
After issuing the fix, the company has revealed details of how users were susceptible to attacks by the malware. “There are many ways that an attacker could place a specially crafted file in a location that is scanned by the Microsoft Malware Protection Engine. For example, an attacker could use a website to deliver a specially crafted file to the victim’s system that is scanned when the website is viewed by the user," read a post on Microsoft’s Security TechCenter.
Further, the company stated, "An attacker could also deliver a specially crafted file via an email message or in an Instant Messenger message that is scanned when the file is opened. In addition, an attacker could take advantage of websites that accept or host user-provided content, to upload a specially crafted file to a shared location that is scanned by the Malware Protection Engine running on the hosting server.”
Hackers exploited Word flaw for months while Microsoft investigated
You can take a look at the list of affected applications here:
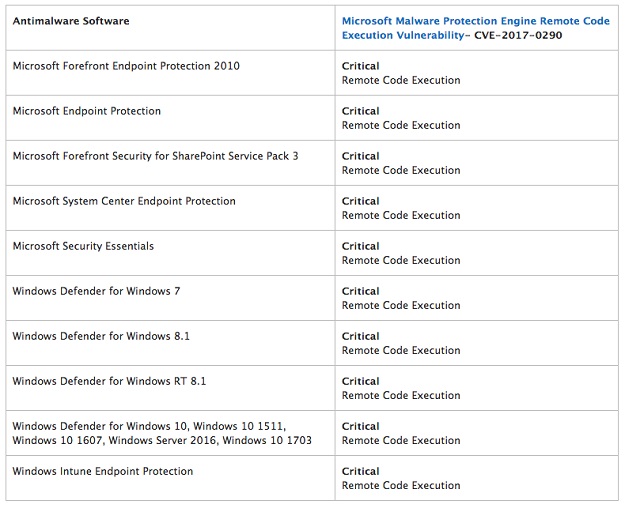 PHOTO: MICROSOFT
PHOTO: MICROSOFTThe fix will reach users over the course of the next two days. Till then you can read Microsoft's detailed post addressing the problem here.
This article originally appeared on The Next Web


















COMMENTS
Comments are moderated and generally will be posted if they are on-topic and not abusive.
For more information, please see our Comments FAQ