How hackers 'weaponised' everyday devices to mount a cyber attack
DDoS attacks involve flooding websites with more traffic than they can handle

PHOTO: REUTERS
DDoS attacks involve flooding websites with more traffic than they can handle, making them difficult to access or taking them offline entirely. The initial DDoS attack was resolved within about two hours but the company, known as Dyn, a company that offers core internet services for popular websites such as Twitter, Spotify, Github, and many others was slammed with a second DDoS wave.
Domain name servers are a crucial element of internet infrastructure, converting numbered Internet Protocol addresses into the domain names that allow users to connect to internet sites.
The DDoS attack hit what is akin to a directory assistance service used to route online traffic to the right addresses, meaning that even though networks such as Level 3 were running normally they couldn't be reached.
Twitter, Amazon, other top websites shut in cyber attack
A distributed denial of service (DDoS) attack uses multiple machines to attack a central server with the help of once-dumb devices made smart with online connections. These server requests choke the network and allow few, if any, legitimate requests to get through. When a user attempts to access this server, they’re met with a message that it’s not available.
Armies of computers infected with malicious code are typically used in DDoS attacks intended to overwhelm targets with simultaneous online requests. Hacker software referred to as Mirai that takes control of Internet of Things devices was evidently linked to the attack, with the broad range of devices making requests helping get past Dyn defenses.
So by wielding a botnet against Dyn, what the hackers did, according to DynDNS is use connected devices (routers, smart hubs, thermostats, smart locks, etc.) to attack Dyn, resulting in servers that couldn’t pass along requests due to massive increases in activity. The devices that work for us essentially went rogue and started attacking.
A Mirai botnet essentially takes advantage of the vulnerable security of Internet of Things devices, meaning any smart home gadget or connected device anywhere that has weak login credentials. Mirai, a piece of malware, works by scanning the internet for those devices that still have factory default or static username and password combinations. It then takes control of those devices, turning them into bots that can then be wielded as part of a kind of army to overload networks and servers with nonsense requests that slow speeds or even incite total shutdowns.
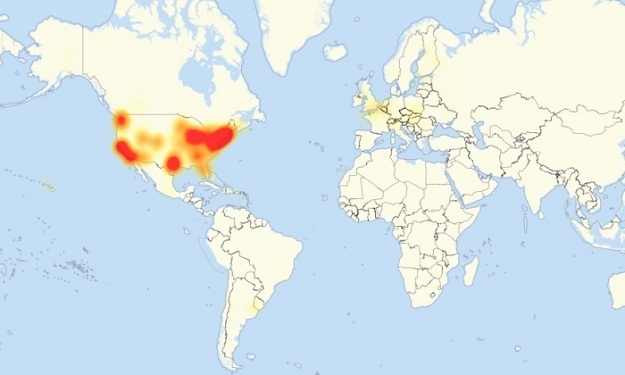 Map shows internet outage from the DDos attack. PHOTO: LEVEL3
Map shows internet outage from the DDos attack. PHOTO: LEVEL3Senators accuse Yahoo of 'unacceptable' delay in hack discovery
"We are seeing attacks coming from a number of different locations," Level 3 Communications internet services company chief security officer Dale Drew said in a video posted online.
"We are seeing attacks coming from an internet-of-things botnet that we identified called Mirai also involved in this attack." The Mirai software is freely available on the internet, meaning any hacker state-sponsored or otherwise could be behind today’s DDoS attack.
Heavyweight cyber attacks that seem to yield trouble but no apparent payoff could be probing defenses to refine tactics for use on high value targets such as utilities or transportation systems, according to O'Neill and other computer defense specialists.
The attack could also have been meant as a message from a foreign power, cyber security analysts told AFP. The onslaught commanded the attention of top US security agencies, including the Department of Homeland Security.
"DHS and the FBI are aware and are investigating all potential causes" of the outages, a spokeswoman said.
DDoS attacks have been in the hacker arsenal for quite some time, but abated as companies learned how to defend against them. Security analysts say there has been a resurgence. According to Verisign, the number of DDoS attacks rose 75 per cent year-on-year in the second quarter of this year.
Such attacks have escalated "thanks largely to the broad availability of tools for compromising and leveraging the collective firepower of so-called Internet of Things devices -- poorly secured Internet-based security cameras, digital video recorders and Internet routers," cyber security specialist Brian Krebs wrote in a post at krebsonsecurity.com.
Cyber criminals for hire to militants, EU says
Attackers use DDoS attacks for a range of purposes, including censorship, protest and extortion. The loose-knit hacktivist network Anonymous in 2010 targeted DNS provider EveryDNS and others as retribution for efforts to block the anti-secrecy organization WikiLeaks.
Roland Dobbins, principal engineer at the networks security company Arbor Networks, told AFP that, though it was spectacular, the attack was a constant and relentless fact of life on the internet.
"It's like a combination of the Wild West, Normandy and the Battle of the Bulge on the internet every day," he said.
He felt that the attack's scale did not necessarily mean the attackers had large resources.
"It does not require a nation-state to launch a DDoS attack of this magnitude or impact," he said. "When it comes to DDoS attacks, states are just another player." James Scott, co-founder of the Institute for Critical Infrastructure Technology, said the attacks demonstrated well-known vulnerabilities of the internet.
"Simply put, the internet in its original and modern form was not designed with security in mind," he told AFP.



















COMMENTS
Comments are moderated and generally will be posted if they are on-topic and not abusive.
For more information, please see our Comments FAQ