CIA could potentially hack your router, according to WikiLeaks
WikiLeaks previously published publications on CIA hacking tools including information on targeting Apple and Samsung

A padlock is displayed at the Alert Logic booth during the 2016 Black Hat cyber-security conference in Las Vegas, Nevada, U.S. August 3, 2016. PHOTO: REUTERS
According to a new document published by WikiLeaks, the CIA has been building and maintaining a host of tools to bypass routers. The documents revealed that a programme called Cherry Blossom was being developed which uses a modified version of a given router’s firmware to turn the device into a surveillance tool for the CIA.
Once the programme functions, Cherry Blossom will let agents monitor the target’s internet traffic, passwords, and may even succeed in redirecting the user to the desired web page.
Shadow Brokers threaten to release Windows 10 hacking tools
WikiLeaks previously released publications on CIA hacking tools, including information on targeting Apple and Samsung.
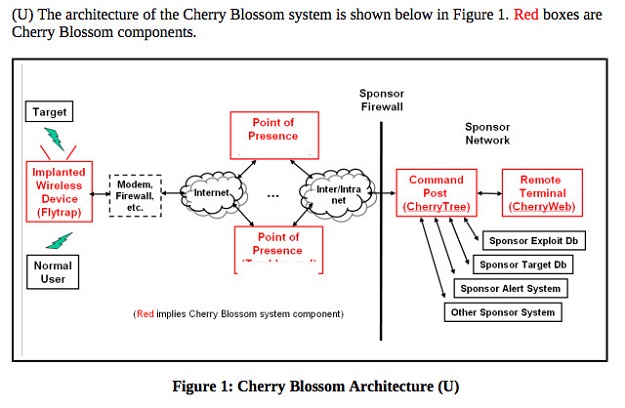
The WikiLeaks document is dated back to 2012 so it's not clear what CIA did with such technology.
Different versions of Cherry Blossom exist, each tailored to a specific brand and model of router.
“As of August 2012, CB-implanted firmwares can be built for roughly 25 different devices from 10 different manufacturers, including Asus, Belkin, Buffalo, Dell, DLink, Linksys, Motorola, Netgear, Senao, and US Robotics,” according to the leaked manual.
The manual also goes into detail on how CIA agents would typically install the modified firmware on a given device. “In typical operation,” another passage reads, “a wireless device of interest is implanted with Cherry Blossom firmware, either using the Claymore tool or via a supply chain operation.”
WikiLeaks source Chelsea Manning released from prison
With increased occurrences of cyber attacks and potentially devastating repercussions seen globally, this technology certainly has a role to play. However, whether CIA used it in a preemptive manner or a preventive manner remains to be seen.
There is also reason to believe the NSA was employing similar tactics with documents published in 2015 by Edward Snowden detailing efforts by the UK’s GCHQ to exploit vulnerabilities in 13 models of Juniper firewalls.



















COMMENTS
Comments are moderated and generally will be posted if they are on-topic and not abusive.
For more information, please see our Comments FAQ