The highly-effective phishing campaign seems to be running on a sophisticated automation feature that pounces on newly compromised Gmail accounts to mount a secondary attack on users in the contact list.
Beware of this latest WhatsApp scam
Once hackers have taken over a Gmail account, they launch their secondary attack by sending out emails disguised under recently sent attachments and a relevant subject line. The email contains a thumbnail version of the attachment which, when clicked, opens up a convincing Gmail login box -- a trap that tricks users in revealing their Gmail account password.
What makes this new technique effective is that the emails are received from someone the victim knows. Further, the attack doesn’t send potential victims to a dodgy website that could be blocked, and features an attachment instead which loads as a full web page.
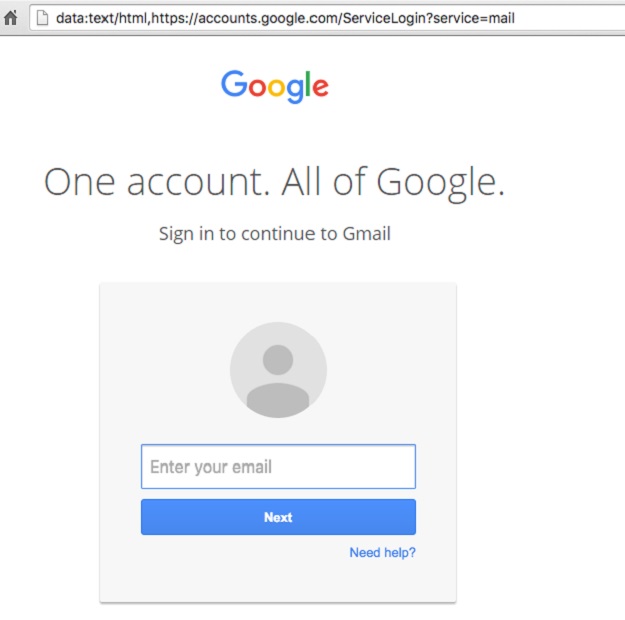 PHOTO: WORDFENCE
PHOTO: WORDFENCEThe browser’s address is also padded with white space, so that victims only see the first part which is enough to convince them to let down their defenses.
Fortunately there is a simple way for users to protect themselves against such attacks. Users can enable factor authentication on their Gmail accounts which would require a secondary factor such as a smartphone when logging into the account.
Yahoo says at least 500m accounts hacked in 2014
Users are also advised to lookout for a lock icon next to the address bar. However, this method is not foolproof as many phishing pages are now hosted on SSL-secured servers and would feature the lock icon as well.
This article originally appeared on Forbes.






















COMMENTS
Comments are moderated and generally will be posted if they are on-topic and not abusive.
For more information, please see our Comments FAQ